Cryptology - Encryption, Hashing, Digital Signatures, Digital Certificates
Encryption & Decryption
A secret or disguised way of writing the actual data is encryption. Deciphering(converting) the disguised data or secret back to the actual data is decryption.How to encrypt the data using encryption?
Data can be encrypted using a encryption(cipher) algorithm associated with a secret key.What is the purpose of a secret key in encryption?
It basically acts as a key to lock(encrypt) the data during encryption and unlock(decrypt) the locked data during decryption.Symmetric encryption:
If we use the same key for both encryption and decryption then we call the process as symmetric encryption. This process uses a single secret key.Asymmetric encryption:
If we use a key pair(private key & public key) and use one key for encryption and the other key for decryption. we call this process as asymmetric encryption.What is the purpose of the encryption(Cipher) algorithm in encryption?
As the name suggests, it contains the algorithm(code) for converting the actual data into an encrypted(secret) data. Examples of encryption algorithms are AES (Advanced Encryption Standard), BlowFish, PBE(Password-Based encryption) etc.Usage:
It is used for protecting/hiding the data which means the users who know the key can only access the encrypted data.Message Digest/Hashing:
Generating a digital fingerprint out of the actual data is called hashing/Message digest. Here are the important characteristics of the hashing are:- No two data generate the same fingerprint
- A very minute change in data generates a different fingerprint altogether.
What is a Digital fingerprint?
A digital fingerprint is called as Hash/Digest/Checksum in software terms. It is the O/P of hashing. It takes the form of byte array and it has a fixed size.How to generate a digest for a data?
For generating a digest of a data, a message digest algorithm has to be used. Message digest algorithm has the algorithm/code to convert the data into a digest/hash. The size of the hash is fixed and it is dependent on the hashing algorithm you choose to generate the Hash. Example of hashing algorithms are MD5, SHA-256 (generates 32-byte hash), SHA-512 (generates 64-byte hash) etc.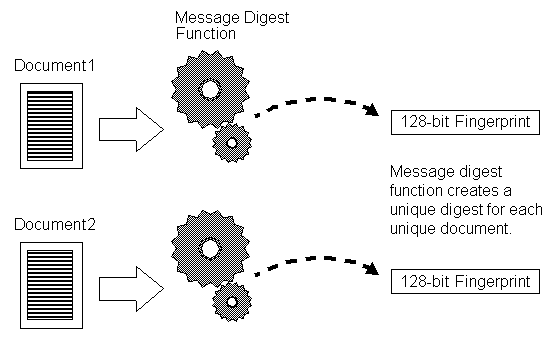
Usage:
MessageDigest is used to check the authenticity of the data during transit. This can be done by generating the digest of the data that you want to transmit and send the digest along with the data. The receiver generates a message digest of the data and compares that with the digest that is being sent. It is used as a modification detection mechanism.What is a Signature?
Digital Signature is similar to a handwritten signature. Just like any other handwritten signature, digital signature also gives authenticity(who owns) and integrity(genuineness/reality) to the message/document. It is unique to that user and that document.To provide authenticity & integrity of the data, Signature has adopted the features of asymmetric encryption and message digest into its algorithm which means the encryption part of the signature protects the data and the message digest part gives assurances about the integrity(genuineness) of the data. In a nutshell, Signature does both encryption and hashing of a data to achieve authenticity & integrity.
How to generate a Signature?
Signature, with the help of a Signature algorithm, initially generates the hash of the data and later it encrypts the hash with a private key. This encrypted hash is the o/p of Signature and it is called as a digital signature of the input data.
Examples of Signature algorithms are MD5WithRSA( where MD5 represents a digest algorithm and RSA represents an encryption algorithm), SHA1WithRSA ( where SHA1 represents a digest algorithm and RSA represents an encryption algorithm).
Usage:
Signature is used to transmit the data in a protected way. A sender who sends the data/document also generate the digital signature(encrypted hash) of the data and send the digital signature along with the original data. A recipient who receives the data should use the public key of the sender to unlock the message and get the hash out of it. Then the hash has to be compared with the computed hash of the original data he received to confirm the validity of the data.What is a Certificate?
A digital certificate is similar to any certificate issued by the governing body like certificate issued by education board, PAN issued by govt, etc.. In the digital world, certificates are issued by trusted third parties like CA, Verisign, etc. These trusted parties are called certifying authorities. An applicant who is seeking a certificate can raise a certificate signing request(CSR) to a certifying authority.What is CSR (Certificate Signing request)?
A CSR contains the public key for which the certificate should be issued, user details(name, organization details, etc.) and a digital signature(which protects the integrity of the public key that the user is sending to the certifying authority). Certifying authority verifies the CSR of the applicant and issues a digital certificate after verification. A digital certificate that is issued to the application has the following contents.- Whom it is issued to (user details)
- Certified Public key (user's public key)
- The digital signature of the certifier (which protects the integrity of the public key).
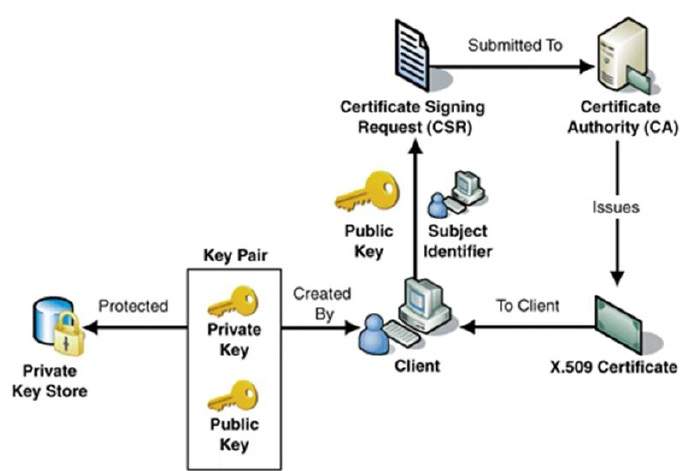
Since the issued digital certificates are signed using root certificates from a trusted CA which means they are signed using the private key of a root certificate. The root certificates which are also available on our OS and browsers will be able to verify the issued certificates. The root certificates in our machines verify the issued certificates using the public key of a root certificate. Once the verification is completed, the browser/OS stores the certificate.
Usage:
Certificates are used to represent the identity and trustworthiness of a website. They are also used for secure socket layer (SSL) communication between a client and a website.SSL communication is achieved by first extracting the public key from the digital certificate of the website. Then a random key is generated by the client and it is transported to the website by encrypting the random key(Symmetric) with the public key of the website. The website receives the encrypted random key of the client, decrypts it. This whole process is called SSL handshaking. This happens before the actual data communication between the client and the website. Once, the SSL handshake happens, both client and website use the random key for encrypting the data.
The reason behind SSL choosing symmetric encryption over asymmetric encryption because Asymmetric algorithms used in asymmetric encryption are much slower than encryption algorithms. They are not suitable for transporting large amounts of data.
For enabling SSL for a website, the certificate issued by CA has to be uploaded to the server which hosts the website.

Comments
Post a Comment